Time ago, we receive a phishing that easily bypassed the Microsoft Exchange Protection (EOP) and a third part email sandbox solution. The technique was an old one, but it was still effective.
TL;DR The file is an encrypted XLSX with a default MS Office password (VelvetSweatshop). With this bypassed some security systems. In this article analyses this encrypted file static and dynamically.
The malicious email contained an attached file who looked as a normal Excel (.xlsx) file. Windows showed the same normal icon to the final user.
The file is that:
- Name: Po No – 60.xlsx
- sha256: d95a8bf886bf7ecfd4a4730728389898d050f684dd4715e5de12cd1cfd4b184e
But if you analyze with “file” command you get that:

So, that wasn’t expected. Because the email hadn’t a password in the message body. Usually a phishing email that use encrypted files (zip with password for example) tells to the victim what is the password in the message body.
Then we have a crypt file and we don’t have any password. How the adversary expect the victim would be open the file?
The answer is: Microsoft Office has a “default password” for cipher documents and I didn’t know :’)
What happen? If the document is “read only” and the document is encrypted, MS Office will try to use first the default password without asking the user. The default password, as you can imagine, is VelvetSweatshop.
Using this technique the adversary can put signature-based security solutions in a bind, but in our case the email sandbox solution too. Why?
Well, bypass the signature-based solution could be expected, because the malicious code is encrypted with the file. But the email sandbox solution (who is make the dynamic analysis) didn’t analyze the file. Apparently is for an optimization issue, for avoid extra processing. If an encrypted file is attached and the password can’t be found in the message body, the file will not be detonated. I came to that conclusion after doing some tests.
Analyzing the file statically
You can download the sample here (password: infected):
https://mega.nz/file/fRBCgK4L#h6HCY3_qshz_r45AS0E2vcrw7mYOOavMQBBwe2sSBY8
- sha256: d95a8bf886bf7ecfd4a4730728389898d050f684dd4715e5de12cd1cfd4b184e
For the analysis firstly we need decrypt the xlsx file. Using the command (tool included in Remnux):
msoffcrypto-tool <input_file> <output_file> -p <password>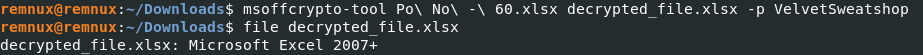
After doing that we can review again with the command “file” and see is a normal xlsx file.
Ok, now the file can be analyzed. The file not contained any VBA or macros.
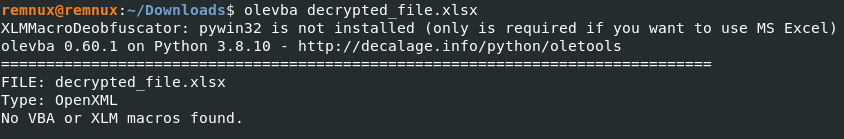
But there are an OLE object.
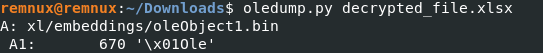
Next we can unzip the xlsx file and review what is “oleObject1.bin”.
Finally with “oleid” command we can analyze the OLE object.
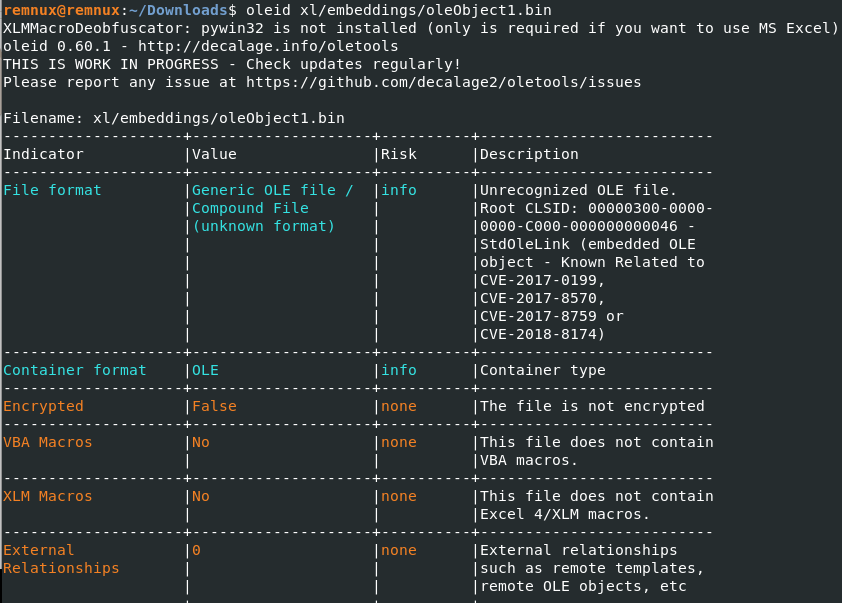
In the “File format” row, the use of an exploit for abuse some vulnerabilities of Office, particularly CVE-2017-0199, CVE-2017-8570, CVE-2017-8759 o CVE-2018-8174 is highly probable.
Analyzing the file dynamically
At the time of this article, the second stage of this threat is not available. So leverage of an older sandbox execution, we can see an expect explotation of “Equation Editor” (EQNEDT32.EXE) and with that a downloaded file.
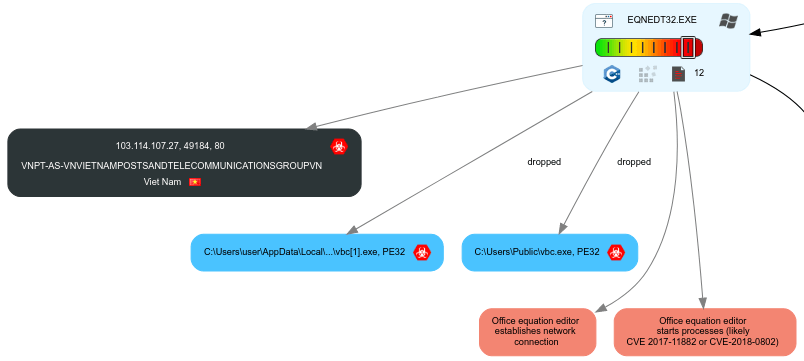
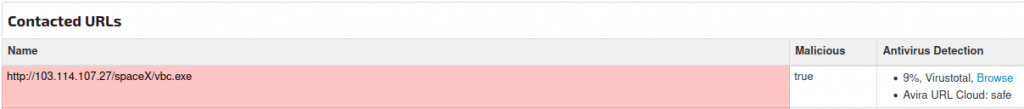
The “vbc.exe” file can be found in this link.
https://mega.nz/file/iU43nZoJ#WJbTuexge-4SgbmMyACOijXcpG-tTNgdWr25B6lm7CA
- sha256: 71ed7ee8f0dca2d6d7b8f03f862a3e730c2c48a84bee4cbf3b9bc35b9b0a5719
VirusTotal tagged this sample as part of “Formbook” family.
With a quickly analysis we see this file is a “Nullsoft Installer” and it can be extracted with “7z”.
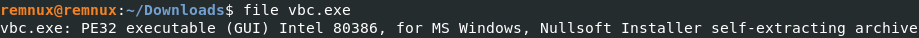
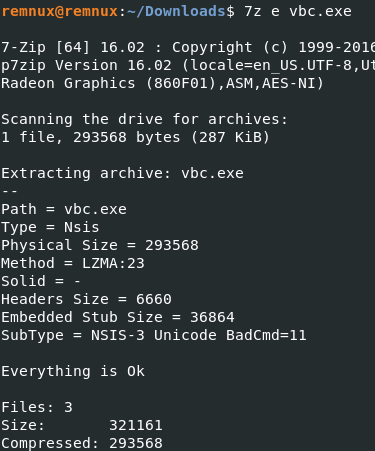
Inside contain 3 files
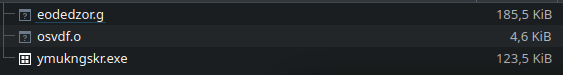
With this hashes:
- 17d2253bad321d809b95eafd085af45f054fce0a7927ee49baa9f60f06668ea9 eodedzor.g
- b99294260a73227b837b563c71385a8bbf90e8378abcd20af7f53d6c32db2804 osvdf.o
- 284bb12e92333d48475e303bcd5823a4fe28835f9a5eb0d8ff3bfa3ea6d89892 ymukngskr.exe
A quickly analysis of capacities, reveal that binary is protected with a XOR function and allocate RWX memory space.
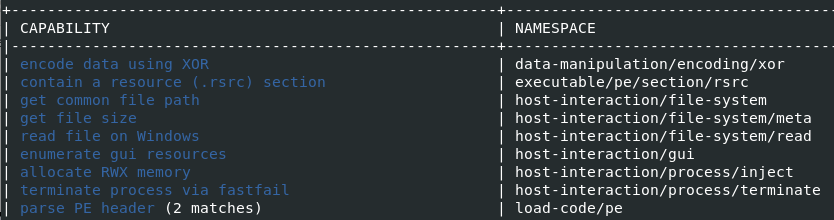
The decrypt XOR process could be a cool future post.

